#5: Containers and Kubernetes - Portainer, Telepresence and Clair
a universal container management platform, a tool for directing Kubernetes traffic to your local machine, and an open-source alternative to Snyk Container
Welcome to Behind the Mutex! Our weekly newsletter summarizes notable activity in open-source, new and growing projects and releases.
In Case You Missed It
Explore the Chroma codebase in our latest review:
The previous issue of our weekly newsletter:
Open Source Landscape
Behind the Mutex picks a few categories and explores new and popular projects and features there.
Containers and Kubernetes
Containers are de-facto the new standard of packaging and distribution of server software. Behind the Mutex is set to be covering the container ecosystem on a regular basis.
Portainer: https://github.com/portainer/portainer
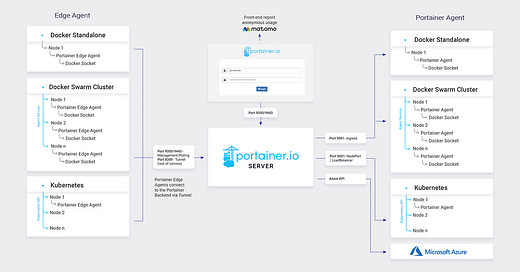
New to containers? Intimidated by innate complexity of Kubernetes and kubectl? Portainer tries to lower the learning curve by introducing a universal container management platform.
The platform helps you run containers in Docker, Swarm and Kubernetes environments using a simple Web UI and API, on your infrastructure of choice.
Portainer consists of two main components: Server and Agent. The Server is responsible for storing metadata about resource configuration and coordination between Agents across environments. An Agent is a management container installed in a given environment, whether it is a Docker host, or a Kubernetes cluster.
In context of Kubernetes environments, Portainer isn’t another Kubernetes distribution. The platform requires a provisioned and deployed cluster and may additionally configure certain resources there.
The system serves a Web UI and API that significantly simplify resource management within a given environment, from creating volumes to installing Helm charts. Users can create their Applications using Web forms that interactively suggest various values depending on other available resources. Portainer also offers a feature that enables automatic Application upgrades based on Git commits to corresponding repositories.
Telepresence: https://github.com/telepresenceio/telepresence
There are many ways to increase your development and debugging velocity in Kubernetes deployments, but Telepresence clearly stands out from the crowd. The tool bridges the gap between a remote Kubernetes cluster and your local workstation. Developers can run their services locally and expose them within clusters, enabling quicker iterations and convenient debugging, all integrated with the rest of the services running remotely.
It is worth highlighting some interesting advantages:
No need to build, push and deploy on every change to your service
Your favorite development environments are at your disposal
No need to run a whole stack locally as you can only replace a single service
Telepresence consists of two components: a CLI tool and a Helm package.
The CLI tool is responsible for:
Instrumenting your target cluster with Traffic Manager, a service that will redirect certain traffic to and from your local machine
Establishing a connection with your cluster and exposing your local machine within the cluster
Intercepting traffic to a remote service and directing it to your local machine
telepresence works seamlessly with your local Kubernetes config:
$ telepresence connect
Launching Telepresence Root Daemon
Launching Telepresence User Daemon
Connected to context default (https://35.232.104.64)And here’s an example of directing traffic from a service within a remove cluster to the port on the local workstation:
$ telepresence intercept hello --port 9000 -- python3 -m http.server 9000
Using Deployment hello
intercepted
Intercept name : hello
State : ACTIVE
Workload kind : Deployment
Destination : 127.0.0.1:9000
Service Port Identifier: 80
Volume Mount Point : /tmp/telfs-524630891
Intercepting : all TCP requests
Serving HTTP on 0.0.0.0 port 9000 (http://0.0.0.0:9000/) ...Clair: https://github.com/quay/clair
If you are looking for a vulnerability scanner for your container images, or want to find an open-source alternative to proprietary solution like Snyk Container, Clair might be a viable option.
The tool offers static analysis of vulnerabilities in both OCI and Docker container images, including images based on Ubuntu, Debian, RHEL, Alpine, AWS Linux and more.
Clair consists of a number of server-side components: Indexer, Matcher, Notifier. They can be deployed as a single service or a collection of distributed services. The system requires a PostgreSQL RDBMS for storing container image reports and other metadata and can be easily deployed onto a Kubernetes cluster.
Users request vulnerability reports by submitting container image manifests into the Indexer service. This can be done via clairctl, or via an HTTP-client (the OpenAPI specification is also available). Once the report is built, the Matcher service tries to correlate vulnerabilities with its database which it keeps up-to-date by periodically pulling updates from various data sources. Then in case the manifest is affected by any vulnerabilities, the Notifier service sends corresponding notifications via Web hooks or AMQP.
$ clairctl report ubuntu:focal
ubuntu:focal found bash 5.0-6ubuntu1.1 CVE-2019-18276
ubuntu:focal found libpcre3 2:8.39-12build1 CVE-2017-11164
ubuntu:focal found libpcre3 2:8.39-12build1 CVE-2019-20838
ubuntu:focal found libpcre3 2:8.39-12build1 CVE-2020-14155
ubuntu:focal found libsystemd0 245.4-4ubuntu3.2 CVE-2018-20839
ubuntu:focal found libsystemd0 245.4-4ubuntu3.2 CVE-2020-13776
ubuntu:focal found libtasn1-6 4.16.0-2 CVE-2018-1000654
ubuntu:focal found libudev1 245.4-4ubuntu3.2 CVE-2018-20839
ubuntu:focal found libudev1 245.4-4ubuntu3.2 CVE-2020-13776
ubuntu:focal found login 1:4.8.1-1ubuntu5.20.04 CVE-2013-4235
ubuntu:focal found login 1:4.8.1-1ubuntu5.20.04 CVE-2018-7169
ubuntu:focal found coreutils 8.30-3ubuntu2 CVE-2016-2781
ubuntu:focal found passwd 1:4.8.1-1ubuntu5.20.04 CVE-2013-4235
ubuntu:focal found passwd 1:4.8.1-1ubuntu5.20.04 CVE-2018-7169
ubuntu:focal found perl-base 5.30.0-9build1 CVE-2020-10543
ubuntu:focal found perl-base 5.30.0-9build1 CVE-2020-10878
ubuntu:focal found perl-base 5.30.0-9build1 CVE-2020-12723
ubuntu:focal found tar 1.30+dfsg-7 CVE-2019-9923
ubuntu:focal found dpkg 1.19.7ubuntu3 CVE-2017-8283
ubuntu:focal found gpgv 2.2.19-3ubuntu2 CVE-2019-13050
ubuntu:focal found libc-bin 2.31-0ubuntu9 CVE-2016-10228
ubuntu:focal found libc-bin 2.31-0ubuntu9 CVE-2020-6096
ubuntu:focal found libc6 2.31-0ubuntu9 CVE-2016-10228
ubuntu:focal found libc6 2.31-0ubuntu9 CVE-2020-6096
ubuntu:focal found libgcrypt20 1.8.5-5ubuntu1 CVE-2019-12904If you have any feedback or would like to see certain open-sources projects highlighted in our upcoming summaries and reviews, please feel free to comment, send an email or DM the author on Twitter @dalazx.
Until next Tuesday,
Behind the Mutex.